Authentication in Picturepark
The Picturepark Content Platform uses a secure authentication system build on Open ID Connect, which allows users to log in to one or multiple different Picturepark Content Platforms with the same Picturepark account, they already use with Picturepark. The Picturepark login is also the preferred method to connect your users with Picturepark Apps, Picturepark Microsites, or via direct user-centric API requests.
Benefits of one Picturepark account for multiple platforms:
One central user repository (Identity Provider) for authentication.
Different permissions per platform role assignments.
Accessing multiple Picturepark platforms with the same account.
One login to connect them all, Picturepark apps and Picturepark Microsites and Picturepark customer systems.
Authentication using highly secure and flexible protocol Open ID Connect.
Easy administration and faster development cycles for new apps.
Picturepark Identity Server (Picturepark IDS)
The Picturepark Content Platform serves the needs of multiple Picturepark customers, where separate user databases become an administrative and security nightmare. For the purpose of saving valuable IT resources Picturepark delegated user authentication and user provisioning to the Picturepark Identity Server (Picturepark IDS) as the default trusted Identity Provider (IdP), connected with Open ID Connect, the industry-standard protocol for secure and flexible authentication. The Picturepark IDS saves all user attributes required to authenticate users in one or multiple different Picturepark Content Platforms.
Copyright Image: Designed by gstudioimagen / Freepik
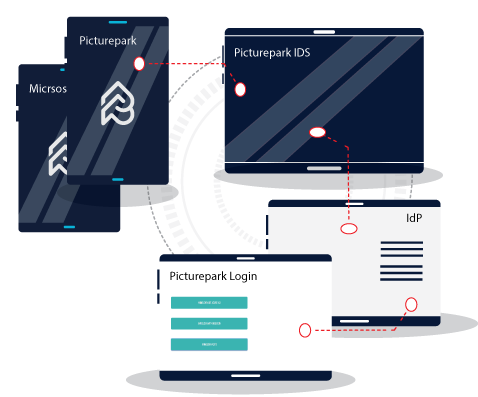
Picturepark IDS Scenario
💻 The user requests access to Picturepark via Login Form.
🏢 The request is sent to the Picturepark IDS which verifies the identity.
🔑 The Picturepark IDS grants or denies access.
Prerequisites
To configure the Picturepark IDS authentication, you need the following items:
A Picturepark subscription.
Configure and test
The Picturepark IDS authentication is inbuilt and needs no further configuration except the creation of a user, either via an administrator or via self-registration on the sign-up form.
Federated Authentication
Instead of only using the Picturepark IDS you can connect an OpenID Provider, which will serve as Identity Provider to the Picturepark IDS. The desired Identity Provider (IdP) must support the standardized Open ID Connect protocol, which itself allows a flexible implementation that varies in required metadata or ACR values.
Benefits of adding an external Identity Provider (IdP):
Linking 3rd party accounts to your Picturepark Content Platform.
Connect to Picturepark quickly, seamlessly, and securely with an existing user account, e.g. from the company Active Directory or any trusted, in-place Identity Provider (IdP).
Add one or multiple supported Open ID Providers easily to your Picturepark.
Full control over permitted Identity Provider (IdP) on a user base, by adding the allowed IdP to the user, e.g. ADFS for employees only, Azure for agencies, and Picturepark IDS for all other users.

Copyright Image: Designed by gstudioimagen / Freepik
External IdP Scenario
💻 The user requests access to Picturepark via IdP button on Login Form, via "Connect via IdP" buttons.
🌍 Picturepark IDS sends the request to the configured Open ID Provider (IdP) which verifies the identity and sends the configured claims.
🔑 Picturepark CP authenticates the user.
Prerequisites
To configure an Open ID provider, you need the following items:
A Picturepark subscription.
A supported Open ID Provider setup and configured, e.g. ADFS on Windows Server 2016.
Limitations
You cannot remove roles from federated users when these roles were assigned from an IdP. Roles must be added to or removed from users via role mappings.
Federated users cannot create API tokens.
Federated users cannot be Invited or set to be "In Review".
The fallback user role of the IdP is only assigned when no role mapping finds a match and there is no default role.
Further Information for External IdP
Picturepark Redirect URL is the URL of the Picturepark IDS + /signin-<Idp-id>
You can see the Picturepark IDS when you open the Login Form of your Picturepark in the URL.
You find the Identity Provider ID in the list of external IdP in Settings > IdP Setup
Client Secret is not needed as Picturepark uses the authorization code flow + PKCE.
FAQ
- FAQ: Why do I need an external Identity Provider?
- FAQ: Why Open ID Connect?
- FAQ: Which external Identity Providers are supported?
- FAQ: What authentication flows are supported?
- FAQ: Is Multi-factor Authentication MFA supported?
- FAQ: Is One Login supported as Open ID Provider?
- FAQ: Is Okta OP supported as Open ID Provider?
- FAQ: Is Google as Open ID Provider supported?
- FAQ: Do I have an inbuilt Identity Provider in Picturepark?
- FAQ: Is Azure AD supported as Open ID Provider?
Glossary Open ID Connect
- Relying Party
Relying Party (short: RP) is an app that outsources the authentication of users, which is Picturepark itself. Picturepark does not handle authentication but outsources authentication to the Picturepark IDS or any trusted Identity Provider configured in the system.
- Picturepark IDS
Picturepark IDS (short: PIDS) is the Picturepark Identity Server, which serves as the default trusted Identity Provider of your Picturepark Content Platform. All identity information (e.g. user attributes) are saved in the Picturepark IDS. You can access multiple Pictureparks with the same identity.
- Open ID Provider
OpenID Providers are implementations based on Open ID Connect, like servers or services or libraries. Open ID Providers are listed on the official Open ID Connect page: https://openid.net/developers/certified. Popular services like Google, Microsoft, or Amazon support Open ID, but each Open ID Provider can define different metadata describing the Open ID Connect configuration. Therefore not all Open ID Providers are supported with Picturepark.
- OIDC
OpenID Connect is a leading standard for authentication, specifically identity provisioning and single sign-on. It uses JSON-based identity tokens (JWT), delivered via OAuth 2.0 flows designed for web, browser-based, and native/mobile applications. OpenID Connect allows clients of all types, including Web-based, mobile, and JavaScript clients, to request and receive information about authenticated sessions and end-users. The specification suite is extensible, allowing participants to use optional features such as encryption of identity data, the discovery of OpenID Providers, and session management, when it makes sense for them. See the Picturepark Open ID Configuration for the live environment, add .well-known/openid-configuration to the identity server URL to get the configuration for your platform.
- Identity Provider
Identity providers (short: IdP, IDP) are systems that manage and maintain identity information (e.g. user attributes). Identity providers offer user authentication as a service. Picturepark outsources the user authentication to the Picturepark Identity Server as the default trusted identity provider and is thus a relying party application to it. See Wikipedia Identity Provider.
- Authorization
Authorization is the process of verifying that "you are permitted to do what you are trying to do" by granting permissions. While authorization often happens immediately after authentication (e.g., when logging into a computer system), this does not mean authorization presupposes authentication: an anonymous agent could be authorized to a limited action set. Picturepark grants permissions via assignments to user roles. See Wikipedia Authorization.
- Authentication Flow
The authentication flow is the definition of how the tokens to identify users are exchanged. Picturepark external Identity Provider must support Authorization Code Flow with PKCE. PKCE, pronounced “pixy” is an acronym for Proof Key for Code Exchange, which does not require users to provide a client_secret. The standard Authorization Code flow would require this. The main benefit is the reduced risk for native apps, as there are no embedded secrets in the source code and this in return limits exposure to reverse engineering.
- Authentication
Authentication is the act of proving that "you are who you say you are" usually done via passwords. The act of verifying the identity of a computer system user. Identity providers offer user authentication as a service. See Wikipedia Authentication.
- ACR Values
ACR Values are optional parameters provided as a space-separated string. These values specify additional context values which the authorization server shall use to process the client request for authentication. If the client provides a value the IdP understands, it will be respected but if the IdP does not understand it, the authentication request is either denied or the acr_values are sent back to the client, which can then decide if the level of authentication is satisfying and carry on with the authentication or reject it. The values appear in order of preference. Possible values may be multi-factor or phishing-resistant. See here for more information: https://ldapwiki.com/wiki/Acr_values.
